Research Article Open Access
A Mathematical Model of Bioterrorist Attack Risk Assessment
Radosavljevic Vladan1,2, Belojevic Goran3 and Jovanovic Larisa4*
1Headquarters of The Serbian Medical Corps, Serbia
2Military Academy, Belgrade, Serbia
3Institute of Hygiene and Medical Ecology, School of Medicine, University of Belgrade, Serbia
4University Alfa, Belgrade, Serbia
- *Corresponding Author:
- Jovanovic Larisa, PhD
University ALFA, Palmira Toljatija 3
Belgrade, Serbia
Tel: 381 64 6125 006
Fax: 381 11 3244 248
E-mail: ecologica@open.telekom.rs
Received Date: April 17, 2011; Accepted Date: July 10, 2012; Published Date: July 16, 2012
Citation: Vladan R, Goran B, Larisa J (2012) A Mathematical Model of Bioterrorist Attack Risk Assessment. J Bioterr Biodef 3:114. doi: 10.4172/2157-2526.1000114
Copyright: © 2012 Vladan R, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited.
Visit for more related articles at Journal of Bioterrorism & Biodefense
Abstract
The authors propose a bioterrorism risk assessment model comprising 22 qualitative and 10 quantitative parameters. Scores 0 and 1 refer to low and high probability of a bioterrorist attack, respectively. Vulnerability analysis is related to targets, while feasibility analysis refers to perpetrators, agents and means/media of delivery. The model is applied on the US anthrax attack in 2001. Mathematical modeling is also proposed to express the risk of human losses in a bioterrorist attack. The model may be helpful in predicting and preventing bioterrorist attacks.
Keywords
Bioterrorism; Risk scoring; Epidemiological mathematical modeling
Introduction
A Bioterrorist Attack (BA) may be presented as a 4-component chain model, including perpetrators, agents, means of delivery, and targets [1]. In continuation to this model, here we propose a mathematical method of Bioterrorist Attack Risk Assessment (BTRA), applied on the US anthrax attack in 2001.
We propose three steps of BTRA: Step 1 (vulnerability analysis related to target); Step 2 (feasibility analysis related to other three components of BA: perpetrator, agent and means/mediums of delivery), and Step 3 (general risk assessment analysis, including all four BA components). A total of 32 parameters (22 qualitative and 10 quantitative) are included in the BTRA (Table 1). Qualitative parameters have specific descriptive characteristics, while quantitative parameters have numerical characteristics. None of these parameters itself constitutes a proof of intentional use of a biological agent, but together they can greatly assist in determining if further investigation is warranted. We have developed a simple scoring system for each parameter. Scores 0 and 1 refer to low and high probability of a bioterrorist attack, respectively.
| Parameter | Risk Score* | ||
|---|---|---|---|
| State or state supported | Disaffected/terrorist groups | Individuals | |
| Target | 1 | 1 | 1 |
| Importance of target | 1 | 0 | 0 |
| Intelligence | 1 | 0 | 0 |
| Secrecy | 1 | 0 | 0 |
| Personal control | 1 | 0 | 0 |
| Control of means/mediums | 1 | 0 | 0 |
| Physical protection | 0 | 0 | 0 |
| Chemical protection | 0 | 0 | 0 |
| Immunological protection | 0 | 0 | 0 |
| Number of people in target | 1 | 1 | 1 |
| Distribution of people in target | 1 | 1 | 1 |
| Location of target | 1 | 1 | 1 |
| Perpetrator | |||
| Sophistication | 1 | 0 | 0 |
| Motivation | 1 | 1 | 1 |
| Ability | 1 | 0 | 0 |
| Capacity | 1 | 0 | 0 |
| Intelligence | 1 | 0 | 0 |
| Secrecy | 1 | 0 | 0 |
| Number of perpetrators | 1 | 1 | 1 |
| Accessibility to sources of agent | 1 | 0 | 0 |
| Accessibility to targets | 1 | 1 | 1 |
| Agent | |||
| A category | 1 | 0 | 0 |
| B category | 0 | 0 | 0 |
| C category | 0 | 0 | 0 |
| Emerging agent | 0 | 0 | 0 |
| Amount of the available agent | 1 | 0 | 0 |
| Means/media of delivery | |||
| Air | 0 | 0 | 0 |
| Food | 0 | 0 | 0 |
| Water | 0 | 0 | 0 |
| Fomites | 1 | 1 | 1 |
| Munition | 0 | 0 | 0 |
| Delivery systems | 1 | 1 | 1 |
| Dispersion systems | 0 | 0 | 0 |
| Total | 21 | 9 | 9 |
* 1 = High probability of a bioterrorist attack (BA)
0 = Low probability of a BA
Total Scores:
1-8 - BA is lowly probable
9-16 - BA is possible
17-24 - BA is highly probable
25-32 - BA is imminent
Table 1: A model of bioterrorism risk scoring.
If we try to calculate all possible BA scenarios with 32 parameters and only two possibilities for each of them (0, 1), there would be 232 ~ 1.000.000.000 possible BA scenarios. These figures explain the complexity of the problem when trying to predict and prevent a BA [2-8]. Mathematical models may be helpful at least in partly solving this problem.
Methods, Results and Discussion
Vulnerability analysis
Vulnerability analysis should be the first step in biodefense strategy [9-12]. It comprises only target as a component of BA, and eleven corresponding parameters (eight qualitative and three quantitative) (Table 1). For biodefense policy makers the very first step should be the classification of targets. There are “hard” and “soft” targets (parameter importance of targets) and three groups of parameters: qualitative (parameters of control, parameters of protection) and quantitative parameters. We will try to explain this analysis on US anthrax attack in 2001. This attack comprised both types of targets: the Hart Senate building in Washington was a “hard” target and the US Postal Offices were “soft” targets. Probability of both types of targets was high for all types of perpetrators (enemy state, terrorist organizations and individuals), so we scored each of them with 1.
Parameters of control are: intelligence/secrecy (global and local), personal control, control of mediums (air, food and water), and control of services/fomites, for example office equipment, postal letters. Intelligence comprises information provided by using electronic surveillance methods, local intelligence systems and observations of possible targets [13]. These systems were posed only by the state, but functioning was missing or someone employed by government could have passed them, so, we scored with 1 only state as a perpetrator. The impact of secrecy has been evident in the aftermath of the 2001 anthrax letters. Although the US Postal Service and the Center for Disease Control knew that the Brentwood postal facility in Washington, DC was contaminated, they waited for four days before closing the facility and treating workers with antibiotics. By that time, one worker had died of anthrax, another was close to death, and two were gravely ill. Another extreme example is China, where the government denied SARS epidemic for six weeks, causing international alarm and spread of the disease in 2003 [14]. This illustrates that government secrecy presents a persistent jeopardy, leaves the public in ignorance, and allows narrow-minded political agendas to undermine health care goals. For these reasons, we scored with 1 only state as a perpetrator.
Personal control comprises physical control of people (their health status) and behavioral control (CV reviewing, control of suspected behavior, control of contacts). In this case, a microbiologist employed in the US Government was a suspected perpetrator again, so we scored with 1 state as a perpetrator.
Control of water comprises use of bottled water and permanent surveillance of central water supply systems. Food control should be performed following the principle “from the fork to the farm” [15]. Air condition systems should also be developed and applied (biosensors). These measures of control were insufficient by State and scored with 1.
Parameters of protection can be physical, chemical or immunological. One form of physical protection of people is the advice to remain indoors in response to biological attack alarm. This will simply prevent transmission of biological agents. Another example is the use of air conditioning systems, or system of increasing air pressure in different parts of buildings [16]. Furthermore, UV radiation sources may be used as physical protection. Chemical protection refers to use of antibiotics, which is a great logistic challenge, since it provides protection only against classic agents (e.g. anthrax or plague), for as long as the available stocks last. Mass immunization program requires careful consideration to assess potential risks and benefits. Nation wide smallpox vaccination campaign, carried out in November 2002 in the USA, was based on the idea of smallpox-infected Iraqis invading America. It resulted in 145 serious adverse events among civilians (hospitalization, permanent disability, life-threatening illness, and at least three death cases [17]. Above mentioned measures of protection were not applied, they did not exist at the time of attack and therefore scored with 0.
Quantitative parameters comprise the number and distribution of people at a target and location of a target. Since overcrowded targets are at highest risk, people must be advised to avoid them (e.g. some manifestations). Potential targets should be safely organized, well protected, located out of a dense urban area, and with easily accessed roads. For each perpetrator they had the same importance, and did exist at the time of attack and scored with 1.
This was an example of a retrograde vulnerability analysis. But, if we know some parameters of any target we can calculate anticipating vulnerability analysis (risk of a successful attack, possible loses, priorities in bio-defense, costs, improvement of resource management).
Feasibility analysis
Feasibility analysis may have dual use (anticipating and retrograde analysis). Anticipating analysis could be used for risk assessment, e.g. as guidelines for biosecurity and biodefense measures [18-20]. It comprises three components (perpetrator, agents and means/mediums of delivery) and corresponding parameters for a BA. Total number of parameters is 21 (14 qualitative and 7 quantitative). Retrograde analysis could be used for finding out a perpetrator and reconstruction of a BA [21].
Three types of perpetrators may exist: government organized and supported perpetrators (institutions and organizations), terrorist organizations and individuals. Other qualitative parameters are sophistication and motivation. Highly sophisticated perpetrators use highly dangerous agents (category A agents or emerging agents) [22], attack without suicidal tendencies, keep themselves unknown, and try to attack “hard” targets. Such perpetrator(s) carried out the USA anthrax attack in 2001. Al-Qaeda was the main suspect the very first day of the attack. But, so high sophistication, ability, capacity, intelligence, secrecy and repeated attacks might have not be expected from Al-Qaeda. Intelligence presents ability to get a true and on- time information on global and local level related to biological attack. Secrecy comprises capacity to keep activities unobserved before an attack, and to keep perpetrators unknown after the attack. Because of that we scored only State with 1. One highly motivated perpetrator was sufficient for all types of perpetrators, so we scored the Number parameter with 1 for all of them. Distribution affects the accessibility of bioterrorists to sources of infectious agents and to their targets. Accessibility of bioterrorists to sources of agent was possible only at the top-secret military labs in Fort Dietrick, so, one point for State. Accessibility of bioterrorist to the targets was possible for everyone through USPS, so we scored all types of perpetrators with 1.
Bacillus anthracis strain used in US attack 2001 was highly specific and stolen from top-secret military labs. Then, only State should be pointed with 1. Also, a repeated attack with this highly selected and sophisticated strain available during longer period of time request solid amount of it. Because of that, we scored only the State with 1. B, C, and emerging agents were not used and were pointed by 0.
Fomites (postal letters) and delivery system (USPS) were used, and could be used by all types of perpetrators, so we scored all of them with 1. Other means/mediums of delivery were not used, and were scored with 0.
This was an example of a retrograde feasibility analysis. But, if we know some parameters of these three components we can make an anticipating feasibility analysis (risk of successful attack, possible loses, priorities in bio-defense, costs, improvement of resource management).
General BA risk assessment
General BA risk assessment may helps in finding out perpetrator, as well as in estimating potential losses due to BA.
Finding out perpetrator. Total number of parameters in Table 1 is 32 (22 qualitative and 10 quantitative). In the US anthrax attack in 2001, (Enemy) State had 66% of the maximum possible number of points, while terrorist organization and individuals each had 28%, respectively.
This difference clearly indicates that someone close to State stayed behind the BA. The risk of BA decreases with increase of the number of known parameters, and the probability of discovering the perpetrator increases with increase of the number of known parameters.
Estimating potential losses and costs is crucial for public health preparedness for a BA. US anthrax attack in 2001, recognized both types of targets: the Hart Senate building in Washington was “hard” and the US Postal Offices were “soft” targets. Losses are known (direct: five dead, 22 ill and 32.000 under antibiotics therapy; indirect: the estimated cost of decontaminating parts of the Hart Senate building in Washington, DC was $23 million (“hard” economic target). The economic impact of a biological attack involving potential exposure to anthrax was estimated at $26.2 billion/100000 persons exposed (“soft” economic target). The cost and resources needed to decontaminate the environment should be added to this [23], as well as losses due to psychological effects [24].
Risk is usually defined as the product of the damage (loss) and probability of its occurrence:
R = p L
p – probability
L – damage (loss)
In the case when the damage (loss) occurs as a result of different causes, the risk is presented as the sum of partial risks:
 (4.1)
(4.1)
Passing to the limit (when the size of the damage / loss depends on a continuous parameter τ) one obtains the following formula:
 (4.2)
(4.2)
Using more detailed mathematical modeling, the risk of human losses due to biological attack can be expressed as follows:
 (4.3)
(4.3)
Here:
R – risk = mathematical expectation of the human losses (E (N))
P – probability of biological attack (accident etc.)
S – area of integration (e.g. territory of the city, district, state,...)
τ – a parameter characterizing the harmful effects (concentration, intensity of the agent)
τ0, τ1 – minimum and maximum values of the parameter τ
p (τ) – the probability of illness/death, depending on the intensity of τ
ψ (x,y) – density of population in the observed area
f (x,y,τ) – density distribution of the parameter τ at the point (x,y) from S
If one takes into account the time factor t (for example, due to changes in the concentration of agent τ, or taking into account the incubation time), the formula gets the form:
 (4.4)
(4.4)
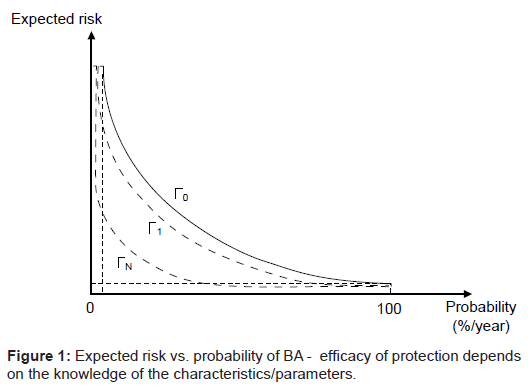
It should be noted that the effective determination of probability is complex and difficult task. It may be estimated on the basis of available statistical data. If the measures of protection/security are taken, the risk reduction is expected. More efficient protection leads to greater risk reduction. Efficacy of protection depends on the knowledge of the characteristics/parameters of the problem: if the larger number of parameters (N) is known - protection is more efficient (Figure 1). Curve ΓN corresponds to the case when n parameters are known. We identified ΓN with a hyperbola where a0 > a1 > a2 >...
where a0 > a1 > a2 >...
The simplest and the cheapest preventive measure in BTRA is vulnerability analysis of the target. It is an independent feasible and useful analysis. Each country could denote its own potential targets as “hard” and “soft” and perform vulnerability analysis.
Conclusion
This paper presents a mathematical model of BTRA that includes vulnerability analysis of targets and feasibility analysis of perpetrators, agents and means/media of delivery. It is also used to express the risk of human losses in a bioterrorist attack. The model may helpful in predicting and preventing BAs.
Acknowledgements
This study has been financially supported by the Serbian Ministry of Education and Science, through projects No. 175078, III47009 and III43009. The authors state that they have no conflict of interest in this study.
References
- Radosavljevic V, Belojevic G (2009) A new model of bioterrorism risk assessment. Biosecur Bioterror 7: 443-451.
- Zilinskas RA, Hope B, North DW (2004) A discussion of findings and their possible implications from a workshop on bioterrorism threat assessment and risk management. Risk Anal 24: 901-908.
- Bossi P, Bricaire F (2006) Biological weapons. Cell Mol Life Sci 63: 2193-2195.
- Radosavljevic V, Jakovljevic B (2007) Bioterrorism--types of epidemics, new epidemiological paradigm and levels of prevention. Public Health 121: 549-557.
- Parnell GS, Borio LL, Brown GG, Banks D, Wilson AG (2008) Scientists urge DHS to improve Bioterrorism Risk Assessment. Biosecur Bioterror 6: 353-356.
- Committee on Methodological Improvements to the Department of Homeland Security’s Biological Agent Risk Analysis, National Research Council (2008) Department of Homeland Security Bioterrorism risk assessment: A call for change. National Academies Press. Washington, DC.
- Ezell BC, Bennett SP, von Winterfeldt D, Sokolowski J, Collins AJ (2010) Probabilistic risk analysis and terrorism risk. Risk Anal 30: 575-589.
- Ezell BC, von Winterfeldt D (2009) Probabilistic risk analysis and bioterrorism risk. Biosecur Bioterror 7: 108-110.
- Sobel J, Khan AS, Swerdlow DL (2002) Threat of a biological terrorist attack on the US food supply: the CDC perspective. Lancet 359: 874-880.
- Alberts B (2005) Modeling attacks on the food supply. Proc Natl Acad Sci U S A 102: 9737-9738.
- Wein LM, Liu Y (2005) Analyzing a bioterror attack on the food supply: the case of botulinum toxin in milk. Proc Natl Acad Sci U S A 102: 9984-9989.
- Nuzzo JB (2006) The biological threat to U.S. water supplies: Toward a national water security policy. Biosecur Bioterror 4: 147-159.
- World MJ (2004) Bioterrorism: the need to be prepared. Clin Med 4: 161-164.
- Guillemin J (2005) Biological weapons and secrecy (WC 2300). FASEB J 19: 1763-1765.
- Beuchat LR, Ryu JH (1997) Produce handling and processing practices. Emerg Infect Dis 3: 459-465.
- Kowalski W, Bahnfleth W, Musser A (2003) Modeling immune building systems for bioterrorism defense. J Archit Eng 9: 86-96.
- Centers for Disease Control and Prevention (CDC) (2004) Update: adverse events following civilian smallpox vaccination--United States, 2003. MMWR Morb Mortal Wkly Rep 53: 106-107.
- Ebright RH, Connell ND (2002) Bioweapon agents: more access means more risk. Nature 415: 364.
- Carr K, Henchal EA, Wilhelmsen C, Carr B (2004) Implementation of biosurety systems in a Department of Defense medical research laboratory. Biosecur Bioterror 2: 7-16.
- Check E (2005) Synthetic biologists face up to security issues. Nature 436: 894-895.
- Kaufmann AF, Meltzer MI, Schmid GP (1997) The economic impact of a bioterrorist attack: are prevention and postattack intervention programs justifiable? Emerg Infect Dis 3: 83-94.
- Rotz LD, Khan AS, Lillibridge SR, Ostroff SM, Hughes JM (2002) Public health assessment of potential biological terrorism agents. Emerg Infect Dis 8: 225-230.
- Zilinskas RA, Carus WS (2002) Possible terrorist use of modern Biotechnology Techniques. Chemical and Biological Defense Information Analysis Center. Washington, DC.
- Radosavljevic V, Radunovic D, Belojevic G (2009) Epidemics of panic during a bioterrorist attack--a mathematical model. Med Hypotheses 73: 342-346.
Relevant Topics
- Anthrax Bioterrorism
- Bio surveilliance
- Biodefense
- Biohazards
- Biological Preparedness
- Biological Warfare
- Biological weapons
- Biorisk
- Bioterrorism
- Bioterrorism Agents
- Biothreat Agents
- Disease surveillance
- Emerging infectious disease
- Epidemiology of Breast Cancer
- Information Security
- Mass Prophylaxis
- Nuclear Terrorism
- Probabilistic risk assessment
- United States biological defense program
- Vaccines
Recommended Journals
Article Tools
Article Usage
- Total views: 15568
- [From(publication date):
July-2012 - Dec 08, 2025] - Breakdown by view type
- HTML page views : 10710
- PDF downloads : 4858